Posts

Learn from Steve Hollands (BQCM) how to become post quantum ready.

Jeroen Prinse

Learn from Ashish Rajan (Kaizenteq) what it takes to secure your cloud environments

Jeroen Prinse

Learn from Paul Watts (ISF) what it takes to be the next generation CISO

Jeroen Prinse
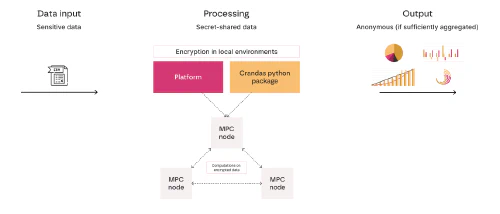
The article explores Multi-Party Computation (MPC). It highlights how MPC allows multiple parties to compute functions over their private data without ever exposing the data itself, maintaining confidentiality throughout the process.

Jeroen Prinse

Learn from Toon Segers, co-founder of Roseman Labs and PhD candidate about Multi-Party Computation

Jeroen Prinse

Learn from world industry expert Sunette Runhaar (Uber) on Insider Threat programs.

Jeroen Prinse
